
Identity and access management with Its necessities
Any organization‘s biggest nightmare can be about its user application becoming compromised and hackers using the employee credentials to access…
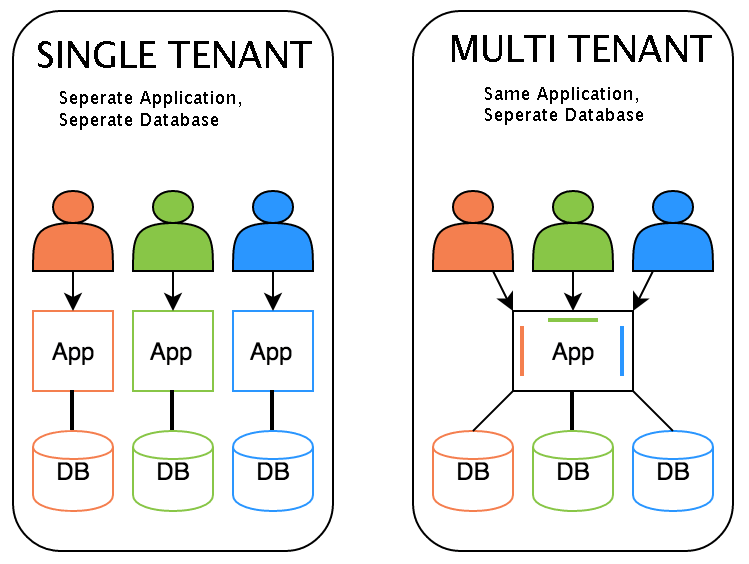
Single versus Multi-Tenant SaaS – Which is Best?
Within a span of few years, SaaS(Software as a Service) has become quite notable. However, subscribers and providers of SaaS…

Security big data
Most of information security efforts focus on monitoring and data analysis with regards to events on networks, servers and other…
SaaS Tenant: Building or Reusing Available SaaS Framework for Your Product
An emerging software delivery model, ‘SaaSTenant™ 2.1’ (Software as a Service) allows developers to leverage their existing .NET assets and…
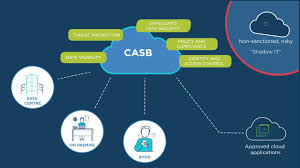
Cloud Access Security Broker ensures application security
Taking the cyber crimes lightly can be a dangerous game for enterprises if they ignore the threats related to cyber…

Idea manifesting your dream-business into reality
When you plan a business, your first concern is investment. Every business aims at profits and Return on Investment (ROI)….
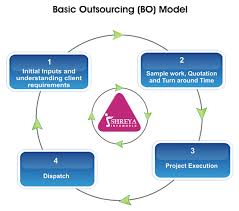
Defusing the Challenges of Tech Companies with Unique Outsourcing Model
In the world of technology, everything gets quickly updated and quickly obsolete. This is beyond devices and platforms and even…

Necessity of Security Operations Center
Nothing guarantees foolproof cyber security as hackers keep on coming with new ideas to breach the barriers meant for cyber…

Front End Web & App Development
When the concept of Internet was new, web-development was for the most part a purely functional data centric endeavor. User…
Single Sign On ensures foolproof security for passwords and user accounts
In a world where cyber criminals are watching over corporate networks, waiting for opportunity to pounce and steal the corporate…
