Taking the cyber crimes lightly can be a dangerous game for enterprises if they ignore the threats related to cyber crimes.
Cyber crimes like data theft and unauthorized data access or network penetration will continue to happen unless all applications, networks, servers and cloud environments are not monitored properly or are not secured via proper security system.
Hence, Cloud Access Security Broker (CASB) is the solution to all problems regarding (and resulting from) unauthorized access and an assurance regarding application security.
What is CASB?
Cloud Access Security Broker is a software tool or service that serves as a moderator between an organization‘s on-premises infrastructure and a cloud provider’s infrastructure.
Acting as a gatekeeper, it analyzes and verifies user behaviour to spot unscrupulous access and allows the organization to extend the reach of their security policies beyond their own infrastructure.
How CASB works?
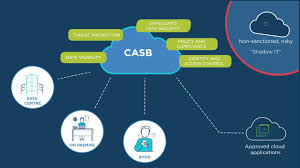
Cloud Access Security Broker ensures that network traffic between on-premises devices and the cloud provider complies with the organization‘s security policies. CASB must be able to give insight into cloud application usage across cloud platforms and unsanctioned use of identity. CASB uses auto-discovery to identify cloud applications in use. It identifies high-risk applications, high-risk users and other key risk factors.
All kinds of Cloud Access Security Brokers may enforce a number of different security access controls. Such controls include encryption and device profiling. They may also provide other services that can include (but are not limited to) credential mapping when Single Sign-On (SSO) is not available for application security.
When corporate data is moved to the cloud and workers of the corporate organization access data from mobile devices, they bypass existing security technologies. This results in a “SaaS security gap” and poses to be a big risk to application security.
Responding to this gap, many organizations use firewall or proxy to block cloud services en masse. However, with thousands of cloud services available today, organizations block the ones that are well known. This causes employees of the organization to seek out and use lesser-known, potentially riskier cloud services that have not being blocked by the organization. CASB solutions can help overcome these issues.
Key pillars of CASB
• Visibility
This functionality gives organizations visibility into users, data, services and devices.
• Compliance
This functionality provides file content monitoring. This monitoring helps organization to find and report on regulated data in the cloud.
• Data Security
Data Security functionality adds additional layer of protection over data that includes encryption.
• Threat Protection
This functionality analyzes traffic patterns to identify compromised accounts and malicious usage.
To know more about Cloud Access Security Broker and the other security services offered by our Security Operations Center, contact us at enquiry@leosys.net or call us at 407-965-5509.